New attacks use Windows security bypass zero-day to drop malware

New phishing attacks use a Home windows zero-day vulnerability to drop the Qbot malware devoid of exhibiting Mark of the Web stability warnings.
When documents are downloaded from an untrusted distant location, this kind of as the Internet or an email attachment, Home windows increase a particular attribute to the file called the Mark of the World-wide-web.
This Mark of the World-wide-web (MoTW) is an alternate info stream that has facts about the file, these kinds of as the URL stability zone the file originates from, its referrer, and its obtain URL.
When a person tries to open up a file with a MoTW attribute, Home windows will display screen a safety warning asking if they are sure they want to open the file.
“Even though information from the Web can be practical, this file style can potentially damage your computer system. If you do not have faith in the source, do not open this application,” reads the warning from Windows.
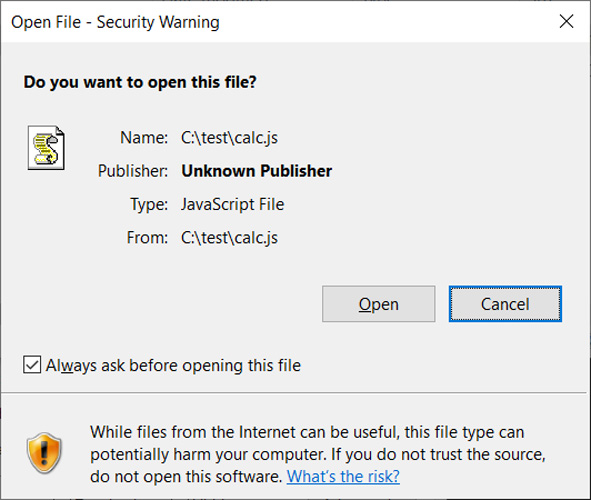
Source: BleepingComputer
Past month, the HP threat intelligence team claimed that a phishing attack was distributing the Magniber ransomware applying JavaScript data files.
These JavaScript files are not the very same as those applied on web sites but are standalone files with the ‘.JS’ extension that are executed using the Home windows Script Host (wscript.exe).
Right after examining the information, Will Dormann, a senior vulnerability analyst at ANALYGENCE, uncovered that the threat actors have been working with a new Home windows



