Hackers have been exploiting a now-patched vulnerability in VMware Workspace ONE Access in campaigns to install various ransomware and cryptocurrency miners, a researcher at security firm Fortinet said on Thursday.
CVE-2022-22954 is a remote code execution vulnerability in VMware Workspace ONE Access that carries a severity rating of 9.8 out of a possible 10. VMware disclosed and patched the vulnerability on April 6. Within 48 hours, hackers reverse-engineered the update and developed a working exploit that they then used to compromise servers that had yet to install the fix. VMware Workspace ONE access helps administrators configure a suite of apps employees need in their work environments.
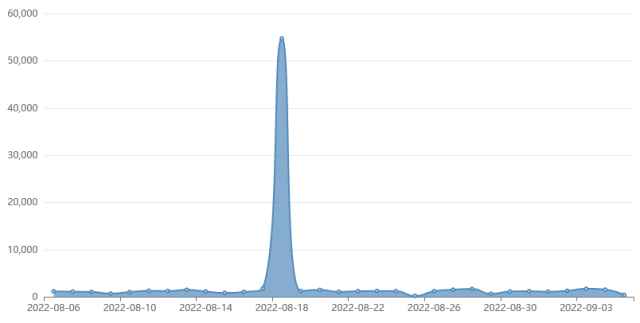
In August, researchers at Fortiguard Labs saw a sudden spike in exploit attempts and a major shift in tactics. Whereas before the hackers installed payloads that harvested passwords and collected other data, the new surge brought something else—specifically, ransomware known as RAR1ransom, a cryptocurrency miner known as GuardMiner, and Mirai, software that corrals Linux devices into a massive botnet for use in distributed denial-of-service attacks.
FortiGuard
“Although the critical vulnerability CVE-2022-22954 is already patched in April, there are still multiple malware campaigns trying to exploit it,” Fortiguard Labs researcher Cara Lin wrote. Attackers, she added, were using it to inject a payload and achieve remote code execution on servers running the product.
The Mirai sample Lin saw getting installed was downloaded from http[:]//107[.]189[.]8[.]21/pedalcheta/cutie[.]x86_64 and relied on a command and control server at “cnc[.]goodpackets[.]cc. Besides delivering junk traffic used in DDoSes, the sample